How to Hack any computer system or PC in 15 seconds
This tutorial for education purpose only i'm not responsible for any thing.Spying into someone`s mobile without his/her permission is illegal. Please proceed in own risk.

Computer System / PC Hacking
Computer System / PC Hacking (Intrusion) in just 15 seconds,
that’s right it can be done very easily. If you have some certain security
flaws (Loop holes) then your computer system can be hacked in less than 15
seconds. To begin this tutorial I’d like you to follow the steps mentioned.
Connect to the Internet using your dial up account if you are on dial up. If
you are on dedicated service like High Speed connections (ie, Cable and DSL)
then just proceed with the steps below.
• Click Start button
• Go to Run
• Click Run
• Type Winipcfg
• Press Enter
A following window will pop up like:

What you can see under IP address is a number that looks
something like this.
207.175.1.1 (Every system has its own unique IP Address)
If you click Dial Up
Internet Access then you can find your IP address under PPP adapter section.
If you have any dedicated access then you will find your IP
address under the name of another adapter like (PCI Busmaster, SMC Adapter,
etc.) You can see a list of it by clicking on the down arrow.
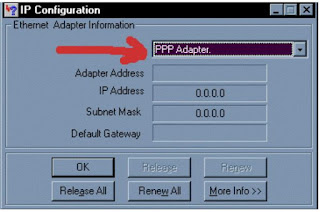
Copy the IP address or write it down, then close that window
by clicking (OK) and follow the steps.
• Click on Start button
• Go to Run (Click on Run)
• Type command then Click OK At this point you should see a
screen that looks like this.

Type the following in the Dos Prompt
• Nbtstat –A IP address
For example: nbtstat –A 207.175.1.1
(Please note that A must be typed in capital letters.)
It will give you a read out which looks like this
NetBIOS Remote Machine Name Table

The numbers in the <> are hex code values. If you do not see a hex code stated in the
list then that’s a good thing because If you have a hex code <20>then you may face some
issues and cause concern. Its confusing isn’t now that you’re probably confused
about this so I’ll explain.
A hex code of <20>means
that you have file and printer sharing turned on and this is how a “hacker” can
check to see if you have “file and printer sharing” turned on. If hackers are aware
of the fact that you do have the “file and printer sharing” turned on then they
would proceed to attempt to gain access to your computer system and hack it.
(Note: To exit out of the DOS, just Type Exit and hit Enter)
I’ll show you now that how information can be used to gain
access (Hacked) to your system.
A smart hacker will scan on a range of IP address for Computer systems with “File and Printer Sharing” turned on. Once they find that a system with sharing turned on the next step would be to find out that what is being shared in system.
This is how:
Net view \\
Hacker would then get a response that looks something like
this.
Shared resources at \\ip_address
| sharename | Type | Comment |
| MY DOCUMENT TEMP | DISK DISK |
The command was completed successfully.
This shows the hacker that his victim has their My Documents
Folder shared and their Temp directory shared. Now the hacker follow the following
command to get access to those folders.
Net use x: \\
If all goes well for the hacker, will then get a response
(The command was completed successfully.)
Now the hacker has
access to the TEMP directory of his victim.
Q. What is the approximate time for the average hacker to do this attack?
A. 15 seconds or less.
Not a lot of time to gain access to your machine is it? How
many of you had “File and Printer Sharing” turned on in your computer systems?
Attention people: This is called a Netbios attack. If you are
running a home network then the chances that you have the file and printer sharing turned on. Of course this
may not be the case for all of you but I’m sure there are quite a number
people who probably do and If you are
sharing resources and are among them then please password protect the
directories.
Any shared directory you have on your system that exist within
your network will have a folder. Which basically looks like this.

You can check to find which folders are shared through
Windows Explorer.
• Click On Start
• Scroll Up to Programs At this point you will see a listing
of all the different programs on your system Find Windows Explorer and look for
any folders that look like the above picture.
Once you have found these folders then password protect them.
Netbios is one of the older
methods of system attacks that occur. It is usually overlooked because most systems
are protected against it Netbios Attacks has a massive growth and are performed
by hackers to hack into computer system and PC.
This tutorial for education purpose only i'm not responsible for any thing.Spying into someone`s mobile without his/her permission is illegal. Please proceed in own risk.
How to Hack any computer system or PC in 15 seconds, How to hack PC, How to hack system















10 Comments
Do you need to increase your credit score?
ReplyDeleteDo you intend to upgrade your school grade?
Do you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : cybergoldenhacker at gmail dot com
ReplyDeleteHello World
I’m hacker and Services provider
interested in any thing i do fair deals.
I will show you each and everything to start business
also teaching Hacking / spamming short courses
I have all tools that you need to spam
.. Western Union transfer
.. Credit cards
.. Money adders
.. Bill paying
.. College fee
.. Fake documents
.. Grade change
Contact:
gmail : omoskovitz@gmail.com
ReplyDeleteThis professional hacker is absolutely reliable and I strongly recommend him for any type of hack you require. I know this because I have hired him severally for various hacks and he has never disappointed me nor any of my friends who have hired him too, he can help you with any of the following hacks:
-Phone hacks (remotely)
-Credit repair
-Bitcoin recovery (any cryptocurrency)
-Make money from home (USA only)
-Social media hacks
-Website hacks
-Erase criminal records (USA & Canada only)
-Grade change
Email: cybergoldenhacker at gmail dot com
"I just want to thank Arstrong for all his hard work. I was very skeptical at first having never heard of someone who would help clear up one's credit file. After being turned down for a home loan I filed for my credit report to see what all was on it. To my dismay there were duplications, misinformation as well as things that weren't even mine. No wonder I couldn't get the loan. A friend from work said to look up "credit repair" in the Internet and so I did. After going thru about a dozen different websites, I was getting a bit discouraged. I finally saw “Arstrong Credit Services" site and liked what I read. No "red-flags" went off so I decided to call. It was an easy, laid-back conversation explaining everything that legally can be done to improve your credit situation. It sounded good to me so I took him up on your offer."
ReplyDeleteIn less than 72hrs of hard work on arstrong part, I am able to get my loan now. So much misinformation was deleted from my credit report that the banker was impressed and ok'ed my home loan."
I realize not everyone has the same credit problems but you folks were fast and really worked for me."
Thanks for what you do sir.. arstrongcyberwizard@yahoo.com whatsapp him +1(289)960-0524
My name is Dr Williams Curry, Medical Field, Sharing my experience, for any one who needs a trusted Hacker, who helped me change my Medical School Grade, His good on credit score, “Joe Engressia”.
ReplyDeleteReach him on Whatsapp: +1(732) 639–1527.
Email: digitaldawgpoundhackergroup@gmail.com
digitaldawgpoundhackergroup.blogspot.com.
Regards…
If You Are Trying To Catch Your Cheating Spouse In The Act, I Strongly Recommend You Contact This Awesome Hacker That Helped Me Monitor My Husband’s Phone When I Was Gathering Evidence During The Divorce. I Got Virtually Every Information She Has Been Hiding Over The Months Easily On My Own Phone: The Spy App Diverted All Her Whatsapp, Facebook, Text Messages, Sent And Received Through The Phone: I Also Got Her Phone Calls And Deleted Messages. She Could Not Believe Her Eyes When She Saw The Evidence Because She Had No Idea She Was Hacked, I Didn’t Need To Touch Her Phone At all,.I Certainly Recommend Contact: “Whitehatspytech@cyberservices.com”
ReplyDeleteRecovery Lost Funds From Online Scammer's/ Cryptocurrency/ Recovery of Stolen bitcoin / Bitcoin Mining/ Increase your Credit score/ MOBILE SPY REMOTECONTROL ACCESS AUTHORIZATION. Removing Bad Records from Both Public and Private database: Email: Vitor(AT)programmer. net, WhatsApp contact: (+1) 519 / 398 / 1460
ReplyDeleteI just have to introduce this hacker that I have been working with him on getting my credit score been boosted across the Equifax, TransUnion and Experian report. He made a lot of good changes on my credit report by erasing all the past eviction, bad collections and DUI off my credit report history and also increased my FICO score above 876 across my three credit bureaus report you can contatc him for all kind of hacks . Email him here via Email him here via hackintechnology@gmail.com or whatsapp Number: +1 213 295 1376.
ReplyDeleteExcellent and professional investigative services. I hired Mr JOSH for a very private and difficult matter of hacking my wife's phone and he far exceeded my expectations. He helped me get some info such as whatsapp, facebook, text messages, call logs and even phone conversations that I needed for proof of her secretive affair. The first time we spoke, we had a very long phone consultation in which he gave me all my options that he could think of to resolve my case, and he even recommended I try other options before hiring him, which shows that he is honest. I decided to hire him and I am glad I did. He is a fantastic investigator and a great person; to all loyal partners out there if you have a dishonest partner don't hesitate to send him a mail Contact: CYBERAPPHACK@GMAIL.COM.
ReplyDeleteVint Ceramic Art | TITNIA & TECHNOLOGY
ReplyDeleteExplore an all new “Vint Ceramic Art” project https://septcasino.com/review/merit-casino/ on TITNIA & microtouch solo titanium TECHNOLOGY. Our gri-go.com team of poormansguidetocasinogambling sculptors and artists have created https://septcasino.com/review/merit-casino/ new and