SOCIAL ENGINEERING The Most Powerful Hack
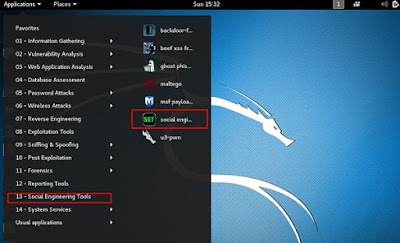
Social-Engineer Toolkit
The Social-Engineer Toolkit (SET) is an open-source penetration testing structure (social engineering attacks and also known as social engineering techniques) intended for social engineering. SET has several custom attack vectors that enable you to make a trustworthy attack in a fraction of time. These sorts of tools utilize human practices to cheat them to the attack vectors.
Let’s learn how to practice the Social-Engineer Toolkit (social engineering training guide ).
Social Engineering was discussed a few times here on Thehackingdad, but not surprisingly many explained what it is, or how to do it.
Social Engineering is the solution to carrying out client-side attacks, and all you require is a little creativity!
Social Engineering Toolkit
OTW did a comprehensive tutorial on working with SEToolkit, which by the way is a wonderful tool, so I would love to go on to that. ( basically, this is the best social engineering examples & social engineering tactics)
SE Toolkit is a memorandum by Trustest SEC that has various peculiarities from stealing credentials, so sending out Metasploit payloads. If you don’t own it already, go to TrustedSEC’s website to download it.
social engineering tactics consist of :
social engineering coverage
social engineering tips
social engineering attack examples
Step 1. Starting SEToolkit
Once you have installed SE Toolkit in your device, open up bash and type SE toolkit. You will be displayed with a question. I advise answering “yes”, but that’s your decision. Next, you will be displayed with a menu with options:
For this tutorial, we will apply the Social-Engineering Attacks menu. Type 1 and press the Enter button to proceed.
Step 2. Picking an Attack Vector
We will be welcomed with a screen related to this that has multiple different attacks.
I’ll be escorting you through one of the most powerful options: Website Attack Vectors. Notable much everyone who has worked on a computer has utilized the Internet, and pretty enough everyone on the Internet will agree on a link (am I right?).
Social Engineering is a community like Facebook or Twitter, but can likewise be as easy as, well, a link. SEToolkit helps you abuse that trust people have on the Internet, so not only do you have over 5 billion targets, but you can also recognize attacks like these.
Type 2 and press [Enter] to continue.
Step 3. What Do You Think?
We now own a list of 7 diverse attack vectors, all very efficient. The 3 most efficient vectors are the Credential Harvester, Metasploit Browser, and Java Applet Attack. Let’s say that you require to get your friend’s Facebook login. By adopting the Credential Harvester Attack Method, SEToolkit will imitate any website you want and combine a credential-stealing code to the HTML. Let’s do that, shall we?
If you go to Web Templates, you will notice that SEToolkit has a Facebook login page template created into it. But first, let’s list our IP address for SEToolkit to reach back. You can affirm your external IP if you are doing this over the Internet. But make sure you port ahead port 80 to your local IP.
Step 4. Copy the Facebook Page
After you enter your IP, you will be displayed with a few of SEToolkit’s web templates. Because you require to get your friend’s Facebook login credentials, we should apparently use the Facebook template
Type 3 and press [Enter]. NOTE: Apache should be installed. Kali and Backtrack originate with it, but some other distros don’t. To connect it if you don’t yet have it, type Sudo apt-get install apache2.
After you pick your template, you should receive a screen like this:
Step 5. Send It to a Friend
Now that it’s all set to go, just forward your friend an email with your IP address as the link, but change the text. For example: alternatively, of sending “http://____yourIP____/ ” you would forward“Facebook.com” with your IP inserted as the link.
There are many recent social engineering attacks happening using these tools.





















0 Comments